Auto logout in seconds.
Continue LogoutI'm subscribed to several online health care news publications. Every week, my inbox is flooded with headlines that cover trends in digital transformation, mobile health, and of course, Covid-19's effect on the industry. But there is another subject that has been popping up far more frequently than I would like: the rapid escalation of health care organizations suffering from network hacking, data breaches, or experiencing a full digital lockdown due to ransomware.
Health care organizations became far more vulnerable in 2020 due to the pandemic, and malicious actors took advantage of the situation. HHS' Office for Civil Rights breach portal shows that in 2020, nearly 530 health care organizations reported a security breach, impacting tens of millions of individuals.
It's scary to watch.
The recent 2020 HIMSS Cybersecurity Survey shows that among 168 U.S.-based health information security professionals, 70% of respondents indicated that their organizations experienced a significant security incident in the past year. The types of incidents are the usual suspects: phishing attacks, credential harvesting, social engineering attempts, and ransomware or other malware.
But while the types of attacks are common, what is striking in the HIMSS data is how 2020 saw a dramatic spike in social engineering and cybercrime efforts compared to 2019, as seen in the table below.

This growth in activity among hackers (+25%) and social engineers (+23%) is likely because of the pandemic, which opened new remote endpoints of employees working from home and gave hackers the opportunity to initiate Covid-themed phishing attacks. Employees are one of the first lines of defense for health care organizations (we covered the importance of revamping staff security training in a previous blog), but also tend to be the most susceptible to security incidents. Rapidly setting up workstations for remote employees expanded the scope of networks and devices connected to health system infrastructure, putting greater pressure on security leaders to maintain a safe and reliable technology platform. Furthermore, the rapid expansion of telehealth has also led to its fair share of security threats as more patients connect with their doctors online.
So, we know that cybersecurity threats will persist—that's a given—but health care stakeholders must continue to focus on improving their organization's security postures. Here are three primary points to keep in mind.
1. Security requires much more than just strong passwords
In addition to the HIMSS survey, there is also the recent release of College of Healthcare Information Management Executives' (CHIME's) 2020 Most Wired Survey, which shows that the percentage of organizations with a comprehensive security program has increased from 24% in 2019 to 34% in 2020 – a respectable jump, but still inadequate. What was notable about 2020's data was the significant growth in the number of organizations with:
- A dedicated cybersecurity committee;
- A documented risk management program that is reported to a board in a formal way; and
- A dedicated security operations center.
CHIME notes that those organizations with comprehensive security programs are more likely than their peers to have implemented various security measures to protect their organization (on average, adoption is 22 percentage points higher than their peers).
Some guidelines have become common sense practices for comprehensive programs: ensure regular technology updates or patches, conduct annual employee training programs, execute backups and ongoing testing, etc. However, the CHIME data shows that comprehensive security programs go beyond technical measures to ensure they have appropriate governance and accountability, dedicated resources, and a designated Chief Information Security Officer.
2. If security is an operational priority, funding needs to reflect that
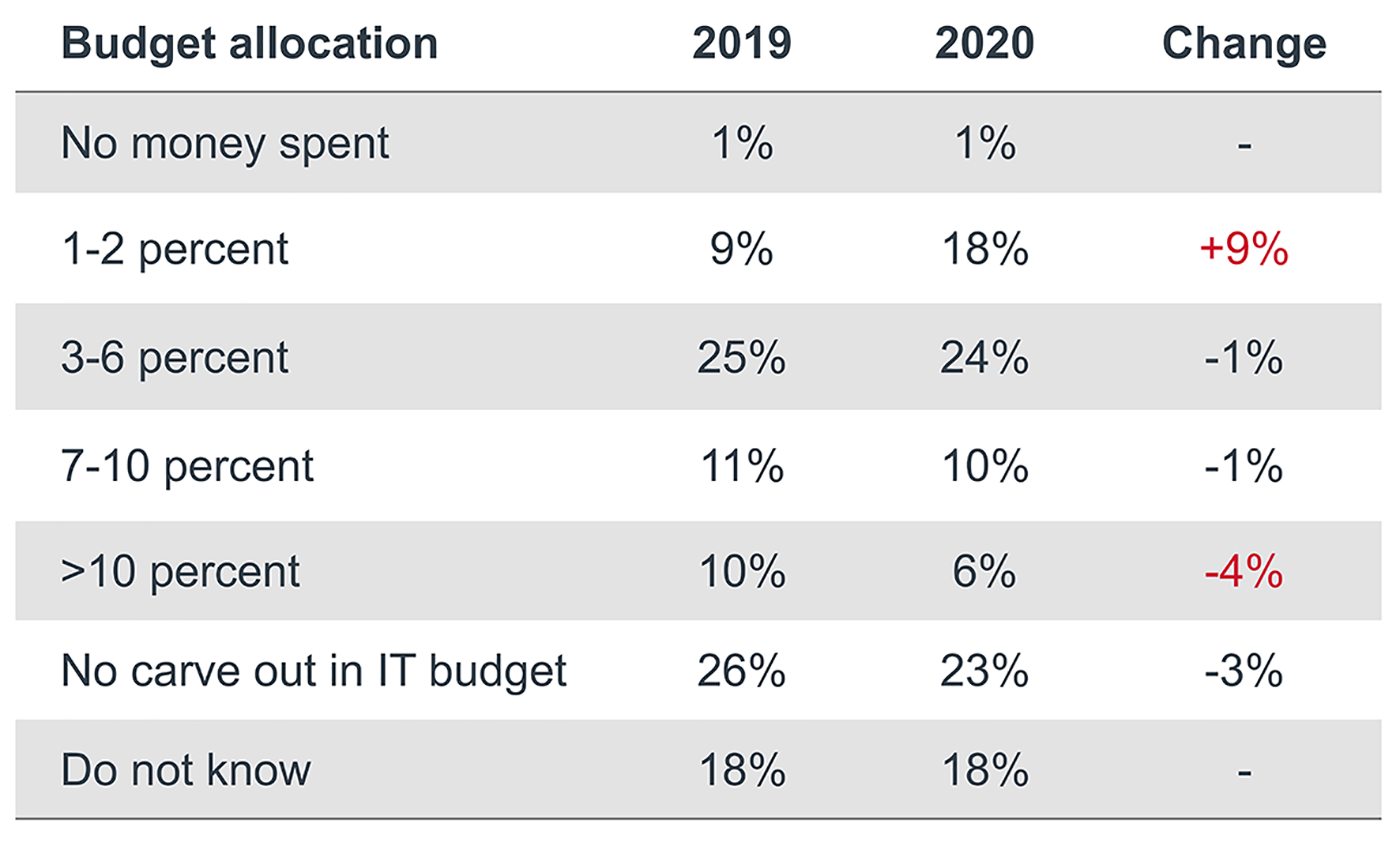
According to the HIMSS survey, the percentage of current IT budgets that are allocated to cybersecurity did not substantially change over the past year for most organizations. However, there was a noticeable increase in programs only allocating 1% to 2% of their IT budgets to security, while there was a 4% drop in those allocating over 10% of their budgets to security (see table below). This data shows that in 2019, 46% of respondents dedicated 10% or less of their IT budget to cybersecurity efforts—this figure jumped to 53% of respondents in 2020. During a year when cybersecurity incidents plagued health care stakeholders, that is a worrying trend.
3. Security leaders must adapt defense protocols to maintain control over the digital ecosystem
Patients, clinicians, and other stakeholders are increasingly digitizing data and processes that on the one hand, can improve patient care and operational decisions, but also increases the surface area for intrusions. Organizational leadership must account for the expanding presence of mobile tools, smart medical devices, and shadow IT.
Third parties also continue to have a growing presence in this digital health ecosystem and pose new risks for many health care providers. This includes not just technology vendors, but managed service providers, subcontractors, or any parties with physical and network access. Hospital and health systems leaders must establish rigorous risk management standards for entering third-party contracts, while continuing to remain vigilant about assessing how these external partners are impacting networks, systems, and data flow. In other words, risk management is not a one-time, up-front activity.
To read further into this topic, see our other blogs on bolstering IoT security and pressure testing third-party risk management programs.
Setting our sights on the new year
We had a tough 2020, but the symbolic shift into a new year brings a sense of renewed motivation to keep security practices top of mind. Consider this blog a push to develop cybersecurity "resolutions" for 2021. For additional information on how to build a cyber-resilient organization, check out our Cybersecurity Resource Library.
Health care organizations are under attack. Vicious threats like ransomware can significantly disrupt or even shut down clinical and business operations at a moment’s notice. While the implications of cyberattacks are often unknown to health care leaders, clinicians, and staff, they are used to handling critical incidents in patient care. Luckily, the process for handling a cyber incident is nearly the same.
Download this infographic to learn how to implement the SANS Institute's PICERL approach to effectively handle cyber incidents.
Don't miss out on the latest Advisory Board insights
Create your free account to access 1 resource, including the latest research and webinars.
Want access without creating an account?
You have 1 free members-only resource remaining this month.
1 free members-only resources remaining
1 free members-only resources remaining
You've reached your limit of free insights
Become a member to access all of Advisory Board's resources, events, and experts
Never miss out on the latest innovative health care content tailored to you.
Benefits include:
You've reached your limit of free insights
Become a member to access all of Advisory Board's resources, events, and experts
Never miss out on the latest innovative health care content tailored to you.
Benefits include:
This content is available through your Curated Research partnership with Advisory Board. Click on ‘view this resource’ to read the full piece.
Email ask@advisory.com to learn more.
Click on ‘Become a Member’ to learn about the benefits of a Full-Access partnership with Advisory Board
Never miss out on the latest innovative health care content tailored to you.
Benefits Include :
This is for members only. Learn more.
Become a member to access all of Advisory Board's resources, events, and experts
Never miss out on the latest innovative health care content tailored to you.



